Category: Cybersecurity
-
In the digital age, there is a dangerous myth circulating in the boardrooms of small and medium-sized businesses (SMBs): “We’re too small to be a target.” While the headlines are dominated by massive data breaches at Fortune 500 companies, the reality on the ground is much grimmer for the little guy. For a global corporation,…
-
The era of the “set it and forget it” antivirus is officially over. For decades, cybersecurity was a game of digital whack-a-mole: a virus would appear, a “signature” would be identified, and your antivirus software would update its database to recognise and block it. But in a world where 450,000 new pieces of malware are…
-
Imagine you are cruising down a highway at 70 mph, reclining in your seat while your car handles the navigation. Suddenly, the steering wheel jerks violently to the left, or the brakes slam on for no apparent reason. You didn’t do it. The car’s software didn’t “decide” to do it. Someone miles away, sitting behind…
-
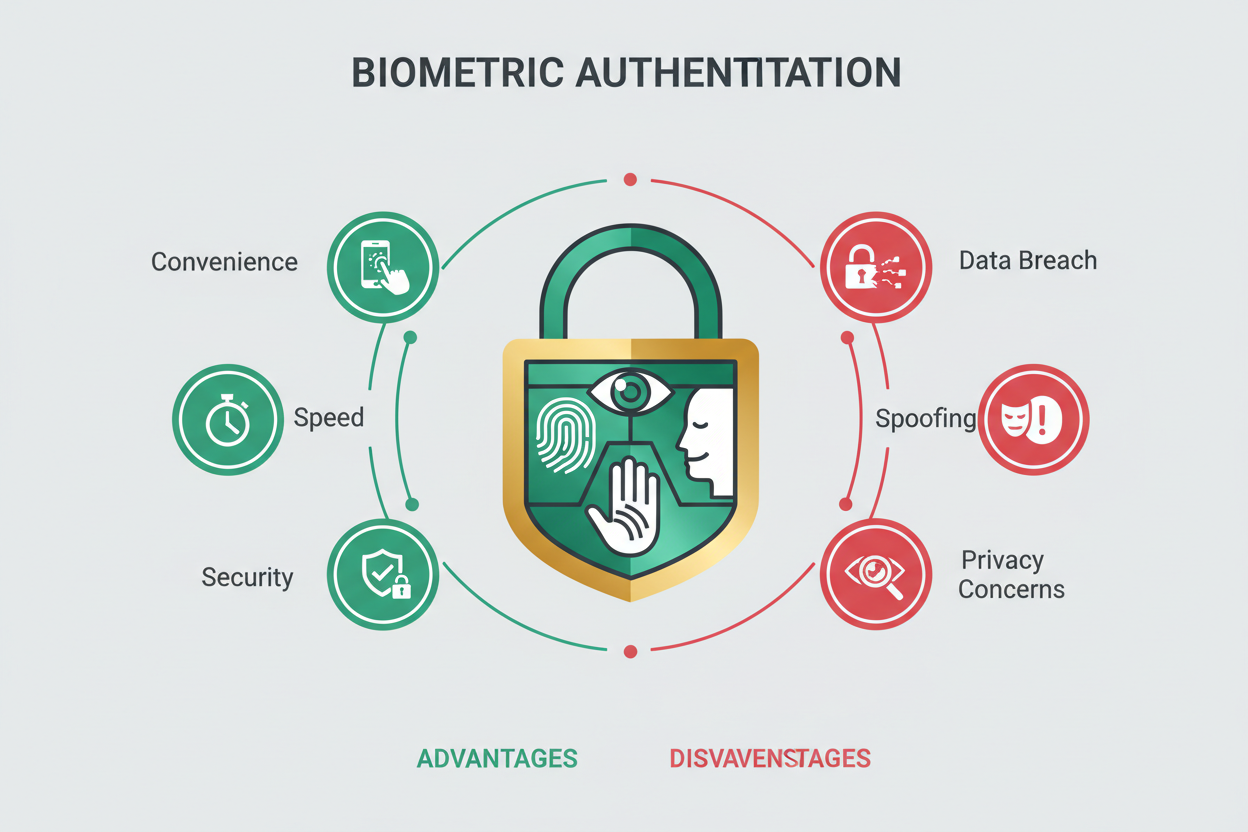
Why Your Fingerprint Might Be Your Best Password—Or Your Worst Nightmare We live in an age of passwords. Dozens of them. Long ones with special characters, numbers, and that one uppercase letter you always forget. We write them down, reuse them, and inevitably forget them. It’s exhausting—and it’s exactly why biometric authentication feels like a…
-
In today’s hyperconnected world, cyber threats no longer arrive only as lines of malicious code or shadowy malware hidden in downloads. Increasingly, they come wrapped in headlines, hashtags, and viral posts. Fake news and misinformation campaigns have quietly become one of the most effective weapons in the modern cyber threat landscape—and their impact on cybersecurity…
-
Your next breakthrough is only as safe as the weakest credential in your company. In an economy where ideas travel at the speed of a click, intellectual property (IP) isn’t just an asset—it’s your competitive moat. Yet the same digital transformation that accelerates innovation has widened every doorway for attackers, insiders, and competitors to walk…
-
Why do smart people still click the wrong link?By ksquared When people picture “hackers,” they usually imagine someone in a dark room breaking into computers with lines of code. In reality, many of the most successful cyberattacks don’t start with code.They start with people. Hackers know that the easiest way into a company or personal…
-
Learn how to keep children and teens safe online with essential cybersecurity tips for families. Discover practical ways to prevent cyberbullying, scams, and privacy risks while building digital confidence. Focus keywords:cybersecurity for kids, online safety for teens, internet safety for children, protecting young users online, parental digital safety tips 🧩 Introduction: The Digital Playground That…
-
When a data breach hits, the clock starts ticking. Your next moves can either turn chaos into control—or make things worse. The good news? With a clear plan and calm execution, you can contain damage, meet legal requirements, and even strengthen trust with customers and partners. Here’s your action-ready playbook for responding to a data…
-
The challenges of securing supply chains A plain‑English guide for the Ksqaured Blog If you’ve ever tracked a parcel and watched it hop between cities, you’ve seen the modern miracle of supply chains. But that neat map hides a messier truth: your stuff depends on a web of farms, factories, warehouses, ships, trucks, software systems,…