Tag: Security
-
Imagine you are cruising down a highway at 70 mph, reclining in your seat while your car handles the navigation. Suddenly, the steering wheel jerks violently to the left, or the brakes slam on for no apparent reason. You didn’t do it. The car’s software didn’t “decide” to do it. Someone miles away, sitting behind…
-
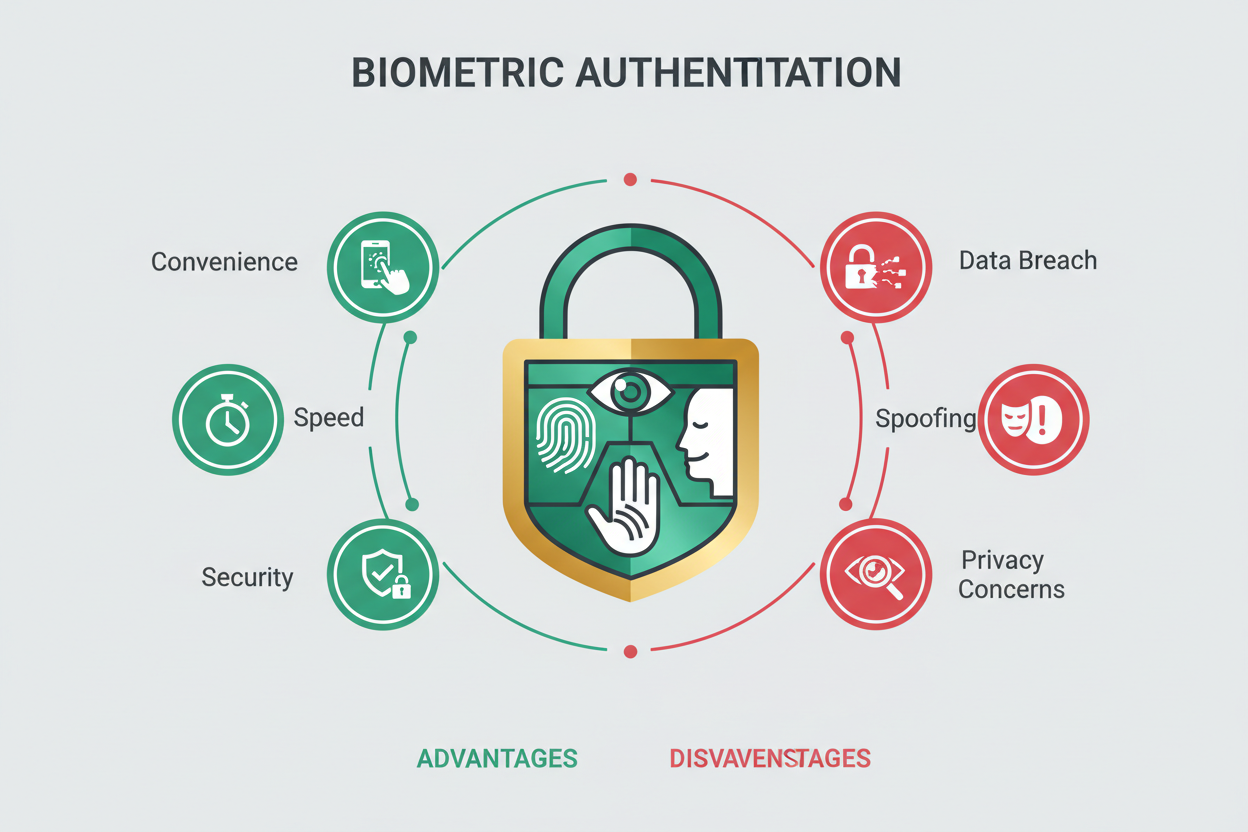
Why Your Fingerprint Might Be Your Best Password—Or Your Worst Nightmare We live in an age of passwords. Dozens of them. Long ones with special characters, numbers, and that one uppercase letter you always forget. We write them down, reuse them, and inevitably forget them. It’s exhausting—and it’s exactly why biometric authentication feels like a…
-
Learn how to keep children and teens safe online with essential cybersecurity tips for families. Discover practical ways to prevent cyberbullying, scams, and privacy risks while building digital confidence. Focus keywords:cybersecurity for kids, online safety for teens, internet safety for children, protecting young users online, parental digital safety tips 🧩 Introduction: The Digital Playground That…
-
Imagine social media as a thrilling high-wire act: one side dazzles with connections, viral moments, and endless scrolls; the other teeters on the edge of privacy pitfalls and cyber chaos. For you and your organisation, it’s not just about likes and shares—it’s a potential gateway for hackers, scammers, and data disasters. In this post, we’ll…
-
Ransomware continues to be one of the most disruptive and costly cyber threats facing organisations and individuals worldwide. As attackers evolve their tactics, it’s crucial to stay informed about the latest trends and adopt robust prevention strategies. In this post, we’ll explore the newest ransomware tactics and share actionable steps to protect your data and…
-
The digital world in 2025 is more connected than ever, but with that connectivity comes a new wave of online scams. Cybercriminals are constantly evolving their tactics, making it crucial for everyone to stay informed and vigilant. Here’s a look at the most common online scams this year and practical steps you can take to…
-
In today’s digital world, cyber threats are rising, making network security more critical than ever. Cybercriminals deploy various forms of network attacks to manipulate, steal, or destroy sensitive information. To effectively protect against these threats, it is essential to understand their nature and implementation. Types of Network Attacks Network attacks can be broadly classified into…
-
Control Techniques Used In Organisation Analysing the benefits, downsides, and feasibility for a range of situations is part of assessing diverse access control strategies employed by businesses. Below is a thorough analysis of many popular access control styles. Mandatory Access Control (MAC) One kind of access control fashion is mandatory access control (MAC), in which access controls…
-
Physical perspective: Physical access control is a term used to describe a method, or the systems and procedures, of limiting physical access to a place or to particular sections inside a building. It guarantees that particular physical places can only be entered by authorised persons with permission. Examples of physical access control include standard door locks…
-
What are project management methodologies? Project management methodologies provide structured approaches for planning, executing, and closing projects. We have four commonly used methodologies: PRINCE2, Rapid Application Development (RAD), Waterfall, and Agile. I will be comparing two methodologies concerning their key features: advantages, disadvantages, and their use as case examples. Below is an explanation of PRINCE2…